Passwords, thanks for being around for 60 years. It is time to retire; we take it from here! Written on

It is uncertain when passwords started being applied in a technology context. Most references mentioned Fernando Corbató as the pioneer in password-based authentication when he developed student access to MIT's Compatible Time-Sharing System. Truth being said, MIT researchers who pioneered the passwords didn't care much about security. At that time, passwords allowed solely to share computational resources among several people.
Of course, in the mid-1960s, passwords were not close in complexity to what is required today. Password complexity has increased over time to improve resilience and security and fight tools developed by cybercriminals or hackers that automate the combination of characters to crack passwords. The longer and more complex the password, the better, since decipher times increase exponentially. Unfortunately, this level of sophistication is usually not even needed to crack a password, as users tend to reuse the same password multiple times or use obvious choices to protect their accounts.
Multi-factor authentication
Multi-factor authentication (MFA) uses more than one factor to authenticate a user. MFA is built by incorporating a combination of:
- Knowledge proof (username, password, access code, etc.)
- Proof of possession (something you own)
- Inherence proof (something you are, such as biometrics)
- Location data (Expected geographical location)
The user security increases as more factors are available in the authentication solution, but also the login time increases, and the user experience decreases.
The security vs. convenience paradigm hasn't yet been solved - until this day!
Frictionless 3FA
At YooniK, we leverage the power of face biometrics to implement our new patent-pending MFA authentication architecture that enables the user to adopt MFA without any associated friction.
Our three-factor authentication (3FA) solution (soon to be 4FA) relies on using person identity-confirming credentials from three separate categories: knowledge, possession, and inherence.
In our SSO blog post, we show how to use YooniK technology to build passwordless authentication in Auth0 as Enterprise Identity Provider. This time we went a step forward to increase authentication security, and we are announcing the YooniK Mobile Authentication!
Check out how simple it is with our demo applications:
- Perform registration on our OIDC server from your mobile device:
 |
 |
- Access from your laptop or any 3rd party device from a trusted service provider to authenticate with YooniK SSO. Insert your user data (knowledge proof) and submit a face picture:
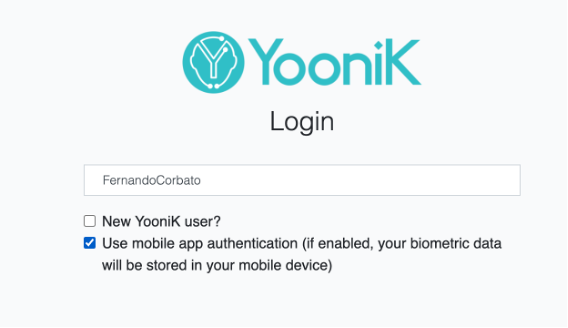
- Receive the notification on your device and tap on it to authenticate (proof of possession):
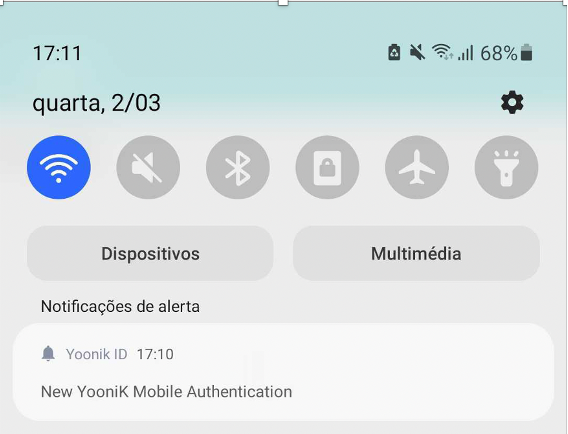
- Finally, our state-of-the-art face authentication algorithm handles inherence proof without any additional action required from the user.

And that's it! Our solution is ideal for user authentication in any use case, ranging from financial services to daily retail checkouts. Our solution offers a unique, secure, and entirely private way to authenticate users.
To get more information and free trial licenses please contact us or join our Discord community.
About YooniK
YooniK simplifies all customer interactions with private, convenient, and secure face authentication on any device. Ranking Top 5 for accuracy in live face matching in the combined business regions of Europe and the Americas, as independently certified by the international benchmark, YooniK enables a fully handsfree experience, bringing unprecedented levels of convenience and accuracy when adopting face authentication in daily routines.
For more information visit the company website or its LinkedIn.






